One of the first things I do when configuring a Linux server is to install denyhosts or fail2ban to safeguard my server from an automated login attack by script kiddies on known SSH ports. Of course, you should absolutely change your default SSH port to something else to prevent some script attacks. denyhosts and fail2ban give an additional safeguard against attackers who are running a brute force attack on your SSH server after sniffing out your SSH port using Nmap. It takes time but it can be done.
Both denyhosts and fail2ban works in similar ways by blocking IP addresses with failed login attempts within a certain period of time. fail2ban comes with a lot more comprehensive options supporting almost all public-facing servers, while denyhosts only concentrates on SSH with limited option. But both will block even legitimate users (as they should) if they have too many failed attempts. Trust me, it can happen to even the best of us whether you mistakenly have the caps-lock ON or forgot that you have denyhosts setup and make too many login attempts on an old password that you forgot you changed. Whatever the circumstances, it can happen.
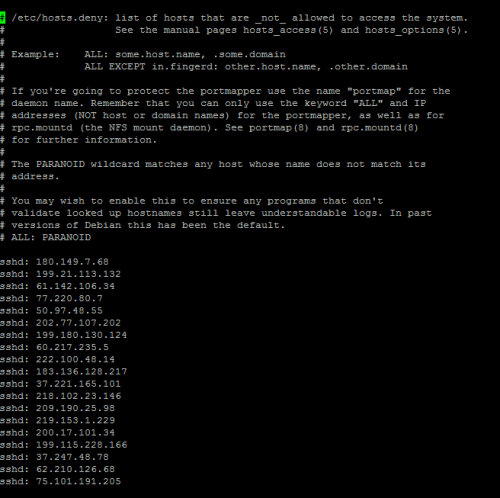
First login (this time don’t screw it up) from a different ip-address. To unban yourself from Denyhosts, edit hosts.deny file nano /etc/hosts.deny and remove your banned ip. To unban yourself from fail2ban use this command iptables -D fail2ban-SSH -s xxx.xxx.xxx.xxx -j DROP make sure you replace xxx with your ip address.